What Is an Operating System? A Beginner’s Guide with Examples
1. Introduction
An operating system (OS) is a software program that manages the hardware and software resources of a computer system. The OS is responsible for managing the computer's memory, processing power, storage, and input/output devices. It also provides a user interface that allows users to interact with the computer and run applications.In this blog post, we'll explore the history of operating systems, the types of operating systems, the functions of operating systems, the components that make up an operating system, virtualization and containerization, security considerations, and the future of operating systems.
2. History of Operating Systems
Operating systems have been around since the early days of computers. The first operating systems were developed in the 1950s and 1960s for large mainframe computers. These early operating systems were designed to manage the computer's resources and provide a user interface for programmers and operators.
As computers became smaller and more affordable, operating systems evolved to support different types of computers, including personal computers and servers. In the 1980s, Microsoft released MS-DOS, which became the dominant operating system for IBM-compatible personal computers. Apple also developed its own operating system, called Mac OS, for its Macintosh line of computers.
In the 1990s, Microsoft released Windows, which quickly became the dominant operating system for personal computers. In the early 2000s, mobile operating systems such as Symbian, BlackBerry, and Windows Mobile were developed for smartphones. Today, the most popular operating systems include Windows, macOS, Linux, Android, and iOS.
2.1. Most Popular Operating Systems in the Market
Microsoft Windows - This is the most popular desktop operating system, with a market share of around 75%. Windows offers a wide range of software and hardware compatibility and is widely used in business and personal computing.
Android - This is the most popular mobile operating system, with a market share of around 85%. Android is developed by Google and is used on a wide range of smartphones and tablets.
iOS - This is the second most popular mobile operating system, with a market share of around 15%. Developed by Apple, iOS is used on iPhones and iPads and offers a range of features and functionality.
macOS - This is the second most popular desktop operating system, with a market share of around 15%. Developed by Apple, macOS offers a range of features and functionality and is popular with creatives and professionals.
Linux - Linux is a popular open-source operating system used on desktops, servers, and embedded devices. It has a market share of around 2%, but its popularity is growing due to its flexibility and customizability.
It is important to note that market share can fluctuate over time, and the popularity of operating systems can vary depending on the region and industry.
3. Types of Operating Systems
There are several different types of operating systems, each designed for specific purposes. The most common types of operating systems include:
Desktop Operating Systems:
These are operating systems designed for personal computers and workstations. They provide a graphical user interface (GUI) that allows users to interact with the computer using a mouse and keyboard. Examples of desktop operating systems include Windows, macOS, and Linux.Server Operating Systems:
These are operating systems designed to run on servers. They are optimized for handling multiple users and managing network resources. Examples of server operating systems include Windows Server, Linux, and Unix.Mobile Operating Systems:
These are operating systems designed for smartphones and tablets. They are optimized for touchscreens and provide a mobile-friendly user interface. Examples of mobile operating systems include Android, iOS, and Windows Mobile.Embedded Operating Systems:
These are operating systems designed for embedded devices, such as smart appliances, industrial control systems, and medical devices. They are optimized for low power consumption and have a small footprint. Examples of embedded operating systems include VxWorks, QNX, and Windows Embedded.
4. Functions of Operating Systems
Operating systems have several key functions, including:
Resource Management:
The OS manages the computer's resources, including memory, processing power, and storage. It allocates resources to applications and ensures that they don't interfere with each other.User interface:
The OS provides a user interface that allows users to interact with the computer. This can include a GUI, command line interface, or touch interface.Application management:
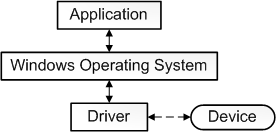
The OS manages applications and ensures that they run correctly. It also provides tools for installing, updating, and removing applications.Device drivers:
The OS provides device drivers that allow the computer to communicate with input/output devices such as printers, scanners, and cameras.Security:
The OS provides security features such as firewalls, antivirus software, and user authentication to protect the computer from malware and unauthorized access.
5. Operating System Components
An operating system is made up of several components, including:
- Kernel:
The kernel can be classified into two types:
- Monolithic - In a monolithic kernel, all operating system services are present in a single executable image.
- Microkernel - In a microkernel, only essential services such as memory management, thread management, and inter-process communication are present in the kernel. Additional services are provided by user-level processes running outside the kernel.
- Device Drivers:
Device drivers provide an abstraction layer between the operating system and hardware components, enabling the operating system to communicate with various hardware components without needing to know the specifics of each device. Device drivers can be written by device manufacturers or by operating system developers.
- File System:
The file system provides several functionalities such as file creation, deletion, modification, and retrieval. It also manages access to files, including permissions and ownership. The file system can be divided into two parts: the file management system, which handles the physical storage of files on the storage device, and the directory management system, which maintains the logical organization of files and directories.
- User Interface:
A GUI provides a visual interface that enables users to interact with the computer through menus, icons, and windows. A CLI provides a text-based interface that allows users to enter commands and receive text-based responses. A touch interface provides a touch-sensitive interface that enables users to interact with the computer through touch gestures.
The user interface also includes system utilities, which are tools that help users manage the computer's resources, such as disk cleanup, defragmentation, and the task manager.
- System Calls:
System calls are implemented through system libraries, which are collections of functions that provide an interface between the user-level application and the kernel. Examples of system libraries include the C Standard Library and the Win32 API.
6. System Utilities:
System utilities are tools that help users manage the computer's resources, such as disk cleanup, defragmentation, and task manager.
6. Virtualization and Containerization
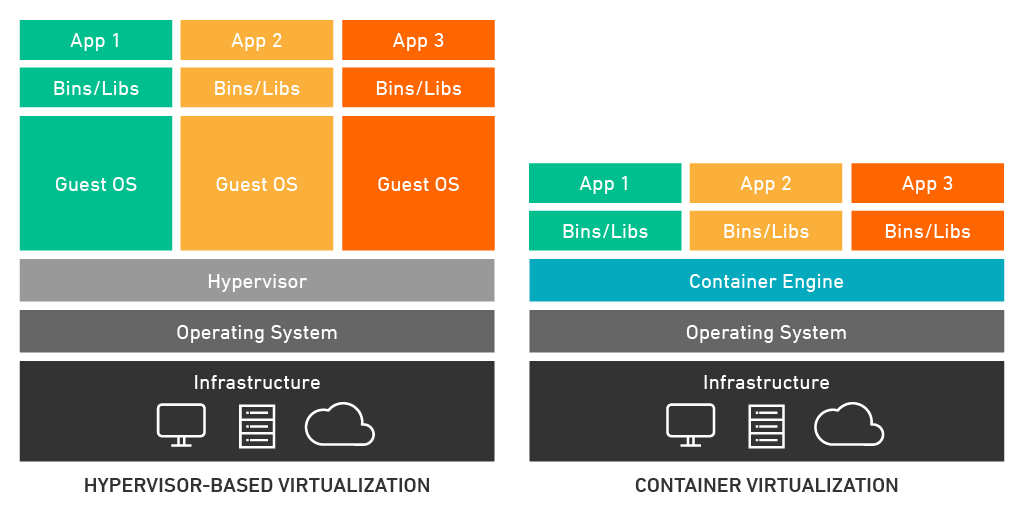
Virtualization and containerization are two popular technologies used to create multiple virtual instances of an operating system.
Virtualization involves running multiple virtual machines (VMs) on a single physical machine. Each VM has its own operating system, applications, and virtual hardware. This allows multiple operating systems to run on a single physical machine, which can be useful for running legacy applications or testing different operating systems.
Containerization is a lightweight form of virtualization that allows multiple applications to run on a single operating system. Each application runs in its own container, which provides a self-contained environment for the application to run in. Containers can be easily deployed and scaled, making them popular for cloud computing and web applications.
7. Security Considerations
Operating systems are vulnerable to security threats such as viruses, malware, and hackers. To protect against these threats, operating systems provide a variety of security features, such as:
1. Firewalls:
Firewalls are an essential component of any operating system's security architecture. Firewalls are designed to monitor incoming and outgoing network traffic and prevent unauthorized access to the computer from the internet or other networks. Firewalls act as a barrier between the computer and the internet or other networks and can prevent unauthorized access to the computer by blocking incoming traffic from unauthorized sources.
Firewalls can be implemented as software or hardware components. A software firewall is a program that runs on the computer and monitors network traffic, whereas a hardware firewall is a dedicated device that sits between the computer and the internet or other networks and filters network traffic.
2. Antivirus Software:
Antivirus software is another critical component of an operating system's security architecture. Antivirus software is designed to detect and remove viruses and other malware from the computer. Antivirus software works by scanning the computer's files and memory for known patterns of malicious code and removing any detected malware.
Antivirus software can also provide real-time protection by monitoring the computer's activity and blocking any suspicious behavior. Antivirus software needs to be updated regularly to ensure that it can detect and remove the latest viruses and other malware.
3. User Authentication:
User authentication is a security mechanism that requires users to enter a username and password to access the computer. User authentication is an essential component of an operating system's security architecture, as it ensures that only authorized users can access the computer.
User authentication can be implemented using various methods, including passwords, biometric authentication, and smart card authentication. Passwords are the most common method of user authentication and require users to enter a unique username and password combination to access the computer.
4. Encryption:
Encryption is a security mechanism that is used to protect sensitive data from unauthorized access. Encryption works by converting data into a format that is unreadable without a decryption key. Operating systems provide encryption tools that can be used to encrypt files and communications.
Encryption can be used to protect sensitive data such as passwords, credit card numbers, and personal information from unauthorized access. Encryption can also be used to protect communications between computers by encrypting data sent over the internet or other networks.
8. Future of Operating Systems
9. Conclusion
Operating systems are a critical component of modern computing. They manage the computer's resources, provide a user interface, and allow applications to run. There are several different types of operating systems, each designed for specific purposes. Operating systems are vulnerable to security threats, and provide a variety of security features to protect against these threats. The future of operating systems is likely to be shaped by emerging technologies, including AI and IoT.









.png)